Introduction
In today’s healthcare environment, practitioners are using state-of-the-art, high-tech equipment that delivers specialty services with better efficiency, accuracy, and overall quality. Using this technology, patients and doctors are also able to generate meaningful data that improves clinical outcomes and, ultimately, the patient’s quality of life.
Despite these improvements in the delivery of care, many healthcare experts are not aware of the vulnerabilities present in connected medical devices. Numerous devices lack proper authentication—the process of validating identities to ensure only trusted users, messages, or other types of services have access to the device. This allows untrusted users to gain access and potentially manipulate the device. Other devices lack basic encryption of the sensitive data being stored in or transferred from the device. These cybersecurity oversights can result in direct harm to the patients and healthcare providers using the devices.
According to security research conducted in 2014 by Scott Erven, head of information security for Essentia, thousands of medical devices in use in healthcare environments are vulnerable to hacking, exposing patients and practitioners to malicious attacks. Erven, among other tactics, used the search engine Shodan to find medical devices connected to the public Internet. What Erven discovered was shocking:
“His team found drug infusion pumps–for delivering morphine drips, chemotherapy and antibiotics–that can be remotely manipulated to change the dosage doled out to patients; Bluetooth-enabled ICDs (implantable cardiovascular defibrillators) that can be manipulated to deliver random shocks to a patient’s heart or prevent a medically needed shock from occurring; X-rays that can be accessed by outsiders lurking on a hospital’s network; temperature settings on refrigerators storing blood and drugs that can be reset, causing spoilage; and digital medical records that can be altered to cause physicians to misdiagnose, prescribe the wrong drugs, or administer unwarranted care.”
Erven’s findings, coupled with similar reports from other medical device security researchers, have raised awareness about the massive vulnerabilities present in connected medical devices. If these vulnerabilities are left unsecured, they put patients in harm’s way and can expose confidential data or compromise an entire hospital network.
Medical device manufacturers need to adopt strong security practices to secure connected devices so patients receiving treatment from them have peace of mind and do not have to worry about malfunctions due to malicious attacks.
Public Key Infrastructure (PKI) is a fundamental aspect of securing IoT devices. As an accepted and well-established standard, PKI is a core component of authentication, data confidentiality, and data and system integrity.
This white paper discusses security risks inherent in IoT devices, and articulates how PKI can be used to mitigate these vulnerabilities and improve the security posture of connected medical devices.
Security Risks in IoT Devices
While delivering on the promise of streamlined efficiencies and operational insights, smart devices in healthcare also present a new and more widespread threat to users and personal data. Current threats to IoT devices have moved beyond simple proof-of-concepts, and it is expected attackers will continue to explore the developments in technology; the ways potential threats can be realistically exploited will accelerate.
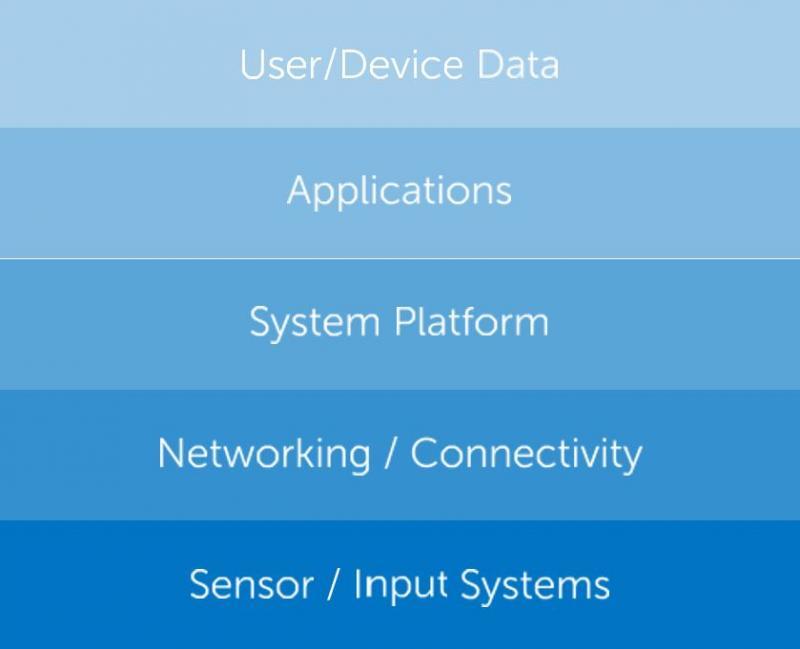
Each IoT device is uniquely identifiable through its embedded computing system but is able to interoperate within the existing Internet infrastructure. Securing these Internet- connected devices and platforms requires a thorough understanding of the makeup of the IoT information stack, its various elements, and the specific security requirements and impact to IoT devices.
For example, an IoT application that collects data from multiple connected devices may have entirely different security requirements than the actual device itself. Security must be considered and addressed throughout each part of a device’s information architecture in the IoT.
OWASP LIST OF TOP IOT VULNERABILITIES
The Open Web Application Security Project’s (OWASP) list of top IoT vulnerabilities demonstrates the critical concern that proper data security, identity, and trust play in developing solutions for the IoT.
The list includes the following as the most critical existing attack vectors for IoT and connected devices:
- Unsecure web interfaces
- Data privacy concerns
- Unsecure device software/firmware
- Insufficient device identity
- User and device identity and authentication
- Unsecure cloud backend systems
- Poor transport encryption
- Implementation
- Unsecure network services
- Unsecure mobile connections
- Poor physical device security
Security implementations are not simply about encrypting data; they also ensure the proper deployment and configuration of security across the various layers of communication within individual devices and across integrated systems.
Security in IoT implementations must be a critical component during the device design and manufacturing phase, or during the initialization phase of a product update. Correctly implemented, secure IoT deployments should ensure that the basic security requirements needed for data confidentiality, data integrity, and data accessibility are properly configured as part of the solution, which is where PKI comes into the picture.
Public Key Infrastructure (PKI): A Proven Solution
Public Key Infrastructure (PKI) is a concept broadly misunderstood in the security world. Many security professionals understand the common uses for PKI—such as authentication, encryption, and signing services—but many fall short in their understanding of how it actually works and is implemented.
PKI FRAMEWORK
PKI is a framework that contains the set of roles, policies, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates. Digital certificates are issued by a Certificate Authority (CA) who acts as a trusted third party. When issued, the certificate is associated with a key pair linked to a user (server, computer, or device) and has an identity that is already verified. Once this identity has been verified, other users can trust the legitimacy of the key holder’s identity.
An example of this concept is a standard-issue U.S. driver’s license. Before issuing the license the state verifies the individual is who he claims to be and that he is fit for driving. If a driver’s license is presented as a form of identification, most parties accept and trust it without question.
A strong PKI framework consists of the following components.
- Certificate Authority (CA) – The entity that stores, issues, and signs digital certificates.
- Registration Authority (RA) – The entity that verifies the identity of other entitites.
- Certificate Policies – Policies created to govern the operation of the PKI.
- Central Directory – A secure location where keys are stored and indexed.
- Certificate Management System – A system that automates digital certificate management.
TRANSPORT LAYER SECURITY (TLS) USE CASE
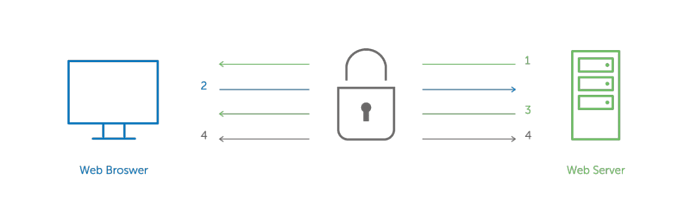
A common use for PKI is Transport Layer Security (TLS)* communications, which is the standard security technology for establishing an encrypted link between a web server and a browser. This secure link ensures all data between the web server and browser remains private. (See graphic.) With the expansion of e-commerce and online banking, and the associated need to securely verify identities, TLS has become a hardened and relied upon security solution.
MOVING BEYOND TLS
PKI has applications well beyond this TLS use case. For example, digital certificates can be provisioned to IoT devices to provide the highest levels of authentication, encryption, and data and system integrity. With no set IoT industry security standards, many experts recommend and rely on PKI for device authentication because of its interoperability.
PKI is a fundamental aspect of security for IoT devices. PKI-based solutions are accepted as a standard for secure communications between users and devices, and have been used to secure servers, fax machines, and other connected devices for decades. PKI offers core security for comprehensive authentication, encryption of sensitive data, and the assurance of data and system integrity. A PKI framework should be the starting point for securing any connected device.
PKI IS FLEXIBLE
While traditional PKI implementations share common threads, like issuing certificates for devices, servers, and clients for authentication and encryption, every IoT implementation can vary in its security requirements.
Device manufacturers need to consider the availability of connectivity, internal device resources, and how these interact with PKI. Some devices will have technical resource constraints or limited availability for regular maintenance and updates.
There are many options for a PKI trust model, which is the security architecture of how trust is established within a deployment. This allows for a variety of approaches for security implementations, making PKI the most flexible solution for securing connected devices. Whether you are working with public or private networks, PKI offers alternative solutions to enable the deployment of the critical authentication and encryption capabilities that ensure privacy and trust.
Historically, TLS X.509 certificates have been the standard— that has not changed. However, with IoT-specific PKI, digital certificates are not under the same restrictions, offering flexible, custom advantages for IoT device manufacturers including the following:
- Custom certificate profiles and key usage fields
- Custom certificate subject fields
- Flexible trusted roots and revocation options
- Shorter and longer validity certificates
- Stronger cryptographic hashes and algorithms
- Direct-to-root chained certificates
Additionally, PKI can be flexible in the way the certificates are provisioned to devices. PKI certificates can be deployed during manufacturing when the manufacturer or CA provisions the certificate to the device. PKI certificates can also be deployed remotely to legacy devices in use by customers through software updates that provision the certificates to enable secure communications between the device and back-end systems.
PKI IS SCALABLE
PKI-based systems have the advantage of broad project application, cross-platform support, and certificate deployment capabilities for projects of various sizes. PKI enables identity authentication, data encryption, digital signing, and device access control, typically out-of-the-box with little internal development by those implementing PKI services. These critical functions are often available in on- prem and hybrid cloud-based platforms to ensure maximum scalability as IoT projects grow in size.
Although unique cryptographic algorithms and flexible certificate options are important functions of PKI systems, IoT implementations need scalable PKI platforms to handle the increased volume and speed of certificate deployments in IoT projects. To meet the critical needs of connected devices, projects must be able to rely on effective, simple, and scalable APIs and systems that can issue not thousands, but millions, of certificates. Performance and availability of these systems vary greatly between available CA software and a commercial CA’s hosted services.
References:
1 Zetter, K. Wired Magazine. “It’s Insanely Easy to Hack Hospital Equipment.” Accessed 6 August 2016. https://www.wired.com/2014/04/hospital- equipment-vulnerable/
2 Shinder, D. “Understanding the Role of the PKI.” Accessed 5 April 2016. http://www.windowsecurity .com/articles-tutorials/authentication_and_encryption/ Understanding_the_Role_of_the_PKI.html.
Cobb, M., Brayton, J., Finneman, A., Turajski, N., & Wiltsey, S. “PKI (public key infrastructure).” Accessed 5 April 2016. http://searchsecurity.techtarget.com/
definition/PKI
*Note: Transport Layer Security (TLS) is the updated cryptographic protocol used to secure web communications. Secure Sockets Layer (SSL) is the predecessor for TLS and is being phased out. Both SSL and TLS are often used interchangeably or referred to as SSL. In this paper, we will use TLS for better accuracy.
4 Anderson, M. “Looking for the Key to Security in the Internet of Things.” Accessed 6 August 2016. http://spectrum.ieee.org/riskfactor/consumer-electronics/standards/looking-for-the-keay-to-security-in-the-internet-of-things